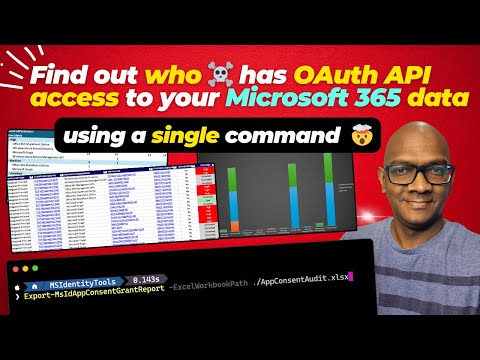
Entra ID - OAuth app audit of your tenant using this command
Product Manager @ Microsoft 👉 Sign up to Entra.News my weekly newsletter on all things Microsoft Entra | Creator of cmd.ms & idPowerToys.com
Secure your Microsoft 365 with one command! Discover how Export-MsIdAppConsentGrantReport simplifies app audits.
Key insights
Quick OAuth App Audit: You can now easily audit what apps have permissions in your Microsoft 365 tenant using the new cmdlet (Export-MsIdAppConsentGrantReport) in the MSIdentityTools module. This tool allows for a detailed review of app permissions and user consents.
- Origin Story: The cmdlet builds upon an Azure AD PowerShell script, improved with an Excel export feature for better data management and now integrated into Microsoft Graph via MSIdentityTools.
- Detailed Permission Review: Through demonstrations and guidelines, it showcases the process to investigate permissions, including per-user delegate consents, and provides risk assessment tips.
- Understanding OAuth 2.0: OAuth 2.0 facilitates a secure authorization mechanism allowing apps to access your data without compromising your login credentials, offering granular control over what information is shared.
- Roles and Process: Outlines roles involved in OAuth 2.0 - You (Resource Owner), Client App, Authorization Server, and Resource Server, along with a step-by-step guide on how the authorization proceeds.
- Benefits and Grant Types: Highlights the security, control, and convenience offered by OAuth 2.0, and explains different grant types suited for various scenarios.
Exploring the Impact of OAuth 2.0 on Digital Security and User Control
OAuth 2.0 represents a significant leap in the way online authorization is handled, providing an added layer of security and control for users across the digital landscape. By eliminating the need to share passwords directly with applications, OAuth 2.0 minimizes the risk of data breaches and unauthorized access. Users can precisely control what data they share and with whom, enhancing the overall security and privacy of online interactions.
This protocol's design caters to a broad specter of applications, from mobile and web apps to device software and IoT platforms, making it a universal standard for secure online authorization. Its flexibility in terms of grant types further tailors the authorization process to the specific needs of each application scenario, providing a perfect balance between security and usability.
Furthermore, OAuth 2.0's widespread adoption by major tech platforms means users enjoy a seamless experience when accessing multiple services, without the hassle of logging in multiple times. For developers and service providers, implementing OAuth 2.0 ensures compatibility and trust with a broad user base, reinforcing the integrity of their platforms.
As digital services continue to intertwine with daily life, understanding and implementing advanced security protocols like OAuth 2.0 becomes crucial. It not only secures data and enhances privacy but also simplifies the user experience across various digital platforms, marking a significant stride towards safe and user-friendly online interactions.
Run a quick OAuth app audit of your tenant with a new command and protect yourself. It has become important to know which apps have permissions in your Microsoft 365 tenant, and performing a quick audit has not always been easy. However, this has changed with the introduction of a new cmdlet.
The new cmdlet, Export-MsIdAppConsentGrantReport, added to the MSIdentityTools module, scans your tenant, reviews app permissions, and the permissions granted to them. This development has its roots in an initial script by Phillipe Signoret, which was enhanced by Michael Epping. This enhancement included creating an Excel export with pivot tables, and has now been updated to work with Microsoft Graph and included in MSIdentityTools.
A guide on how to perform an audit using the cmdlet is provided. It includes steps like installation of MSIdentityTools, running the audit command, and understanding how to review permissions. The importance of configuring risk ratings and how to review user delegate consents is also discussed. This method provides a clear route to enhancing the security measures in your Microsoft 365 tenant.
OAuth 2.0 is presented as a secure method of online authorization that allows you to grant access to your data on one platform without sharing your password with another. This protocol acts like a digital maestro, ensuring a secure exchange of information between apps and services. The process involves a series of steps that maintain the security of your data while granting necessary access to chosen applications.
OAuth 2.0's process starts with you requesting access to your data through a client app, which then directs you to log in through an authorization server. Upon logging in and consenting to share certain data, the authorization server presents an authorization grant to the client app. This grant is exchanged for an access token, which the client app uses to access the designated data on the resource server.
The benefits of using OAuth 2.0 include enhanced security, as there's no need to share passwords. You gain granular control over what data to share and with whom. It also provides convenience by allowing seamless access across different platforms without the need to re-enter credentials. OAuth 2.0 is widely adopted, ensuring compatibility across various services.
There are different grant types within OAuth 2.0, each suitable for specific scenarios. These include the Authorization Code Grant for web applications, the Implicit Grant for client-side apps, the Resource Owner Password Grant for trusted clients, and the Client Credentials Grant for machine-to-machine communication. Each of these grants caters to different security and application needs, like choosing the right musical style for a performance.
OAuth 2.0 orchestrates a complex yet secure interchange of data between platforms, acting as a crucial component in modern online security. Understanding its workflow and benefits can significantly enhance how you manage access to your data across different applications.

## Questions and Answers about Microsoft 365
Keywords
Run a quick OAuth app audit of your tenant using this command and protect yourself, OAuth app audit, protect tenant, audit command, tenant security, OAuth protection, quick audit, app security audit, secure OAuth app, OAuth audit tools