Microsoft Entra - Conditional Access through Privileged Identity Management (PIM)
Principal Cloud Solutions Architect
Master Microsoft Privileged Identity Management and integration with Conditional Access, ensuring secure privileged operations in Entra ID, Azure, and more!
In John Savill's (MVP) YouTube video, he explains in-depth about integrating Privileged Identity Management (PIM) with Conditional Access in Microsoft's suite of cloud services. PIM is a potent service that aids in managing, controlling, and monitoring access to crucial resources within your organization.
These resources can exist within Microsoft Entra ID, Azure, and other Microsoft Online Services, including Microsoft 365 and Microsoft Intune. The main objective of deploying PIM is to reduce the number of people accessing secure information, thereby limiting any chance of malicious actors gaining access, or authorized users mistakenly impacting sensitive resources.
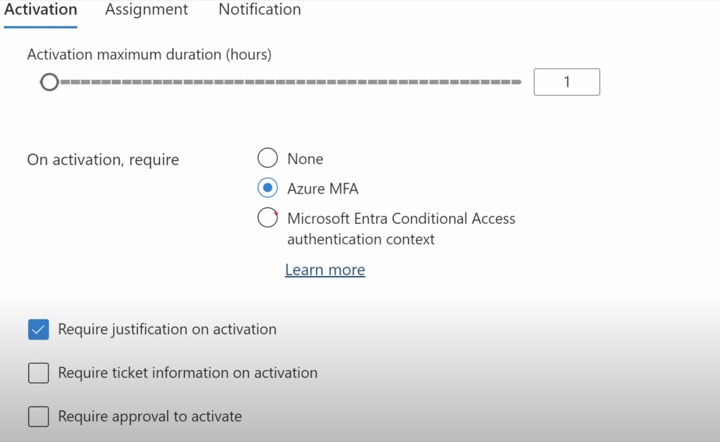
Privileged Identity Management offers time-based and approval-based activation of roles to counteract the risks associated with unnecessary or misused access permissions. It offers functionalities like giving just-in-time priviledged access to Microsoft Entra ID and Azure resources, enforcing multi-factor authentication for any role activation, and conducting regular access reviews.
Administrators looking to manage Microsoft Entra roles within PIM should note that only a user who is either a Privileged Role Administrator or Global Administrator has the rights to manage assignments for other administrators. For Azure resource roles in PIM, a subscription administrator, a resource Owner, or a resource User Access administrator would manage assignments for other admins.
Understanding the Privileged Identity Management system also involves familiarizing with certain terms and concepts. 'Active' is a role assignment that doesn't require any action from the user to use the role, while an 'Eligible' assignment indicates a need for the user to perform certain actions to use the assigned role. 'Just-in-time (JIT) access' follows a model where users obtain temporary permissions to execute privileged tasks, which are revoked once the assigned task is completed.
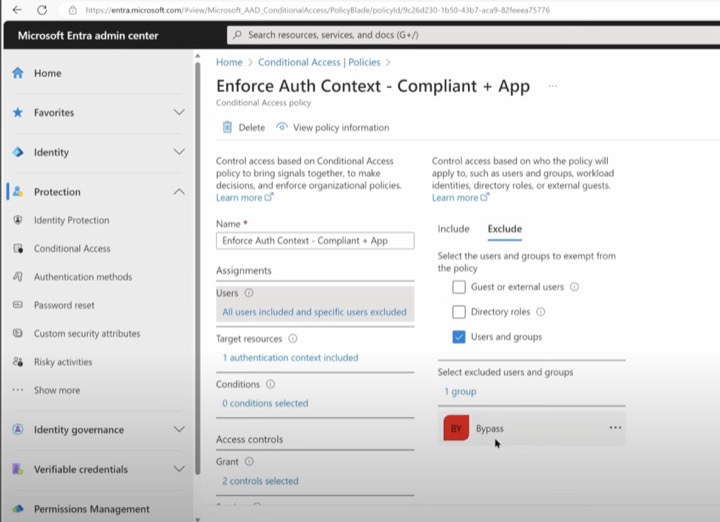
- Azure AD PIM and Conditional Access Integration
- In this step-by-step guide learn how to integrate Azure AD PIM and Conditional Access by using conditional access authentication context.
- Configure Microsoft Entra role settings in PIM
- PIM settings have On activation, require Microsoft Entra Conditional Access authentication context configured, the Conditional Access ...
The PIM role assignment system outlines a reliable means to grant access to resources within your organization, featuring processes such as extending and renewing assignments, assign roles to members, activate assignments, and approve or deny requests. PIM ensures the concerned parties are informed timely by sending appropriate email notifications for any assignments or requests.
PIM: Expanding the Horizon
In a recent update, PIM has expanded its reach to allow for the assignment of eligibility for membership or ownership of PIM for Groups, providing a diversified policy approach to better handle the needs of in-house employees as well as guests. It now provides workload-specific administrators quicker access to multiple roles through a single just-in-time request.
Moreover, you can invite guests and assign Azure resource roles in Privileged Identity Management. Specifically, Microsoft Entra guest users are a key part of the business-to-business (B2B) collaboration capabilities within Microsoft Entra ID. This allows you to manage external guest users and vendors within your organization.
This system allows external vendors the ability to access your Azure resources for project-related tasks, assign external partners or support engineers (even those not part of your organization) to access your resources temporarily for issues troubleshooting and more. PIM seems committed to secure your organization's resources, making it a vital tool for any modern enterprise.
Click here for comprehensive information on enhancing security parameters using Microsoft Entra services.

Entra Privileged Identity Management (PIM)
In this YouTube video, we delve into the integration of Privileged Identity Management (PIM) with Conditional Access, bringing together two key components of Microsoft security. The video explores details about Microsoft Entra's Privileged Identity Management, its capabilities, usefulness, licensing requirements, and additional features. The importance of monitoring and controlling access to crucial resources is examined, through Microsoft Entra ID, Azure, and other Microsoft Online Services. Essential functions of PIM, along with some critical features, are also covered.
- PIM capabilities include assessing when privileged tasks are being performed while ensuring that the concept of 'least privilege access' is adhered to, thereby minimizing security risks.
- PIM also keeps organizations informed by sending email notifications about actions such as assigning roles and approving requests.
- Moreover, it further provides the flexibility of having different just-in-time policies for different group assignments, thereby ensuring optimum security for different classes of users.
If you are willing to deepen your understanding of this subject, Microsoft offers various training courses. For instance, an appropriate course is the "Microsoft 365 Identity and Services" training course, which has a comprehensive module on securing access and managing identities. Remember to always ensure that the course you opt for is aligned with your learning goals.
Understanding the Microsoft Entra suites and related functionalities are significant for anyone seeking to manage and monitor access to important resources. This YouTube video effectively demonstrates both the theory and practical aspects of Privileged Identity Management in conjunction with Conditional Access.
Microsoft's security solutions offer powerful tools to protect organizations from potential risks. The video thus serves as a stepping stone for anyone planning to dive into this domain to enhance their competence, while implying the premium that Microsoft places on secure infrastructures.
Should you have any further discussions on this topic, don’t hesitate to explore deeper into Microsoft's Knowledge Base or reach out to their Support. It is also always recommended to keep yourself updated with their latest security best practices and stay regularly informed about their newest offerings. Further understanding can also be built by joining related forums and communities where Microsoft experts are daily discussing and sharing their knowledge.
You should also be aware about:
- Assigning Microsoft Entra roles, Azure resource roles, and Eligibility for PIM for Groups
- Activating Microsoft Entra roles, Azure resource roles, and PIM for Groups roles
- Approving or denying requests for Microsoft Entra roles, Azure resource roles, and PIM for Groups
- Extending or renewing Microsoft Entra roles, Azure resource roles, and PIM for Groups.
Lastly, you can further explore the Microsoft Entra guest users feature as a part of your deep-dive into Microsoft Access Security systems. This feature manages external guest users and vendors as guests in Microsoft Entra ID, controlling access to specific Azure resources for a project. Therefore, gaining an in-depth knowledge about these functionalities would allow you to effectively utilize Microsoft's security services.
Microsoft is continuously evolving its services and roles. This requires staying updated through articles, forums and by participating in community events. The ultimate goal is to ensure an organization's systems remain secure at all times. Therefore, this concludes our comprehensive analysis of the topic of this YouTube video, leaving you with all necessary knowledge needed about Privileged Identity Management and Conditional Access in the Microsoft universe. Remember, security always comes first and Microsoft surely knows how to provide it!
Keywords
Privileged Identity Management, Conditional Access, Integrating PIM, Conditional Access Integration, Identity Management Solutions, Advanced Security Access, Secure System Access, PIM and Conditional Access, Enhanced Security Integration, Privileged Identity Protection.