Boost Security with Conditional Access Template Guide
Principal Cloud Solutions Architect
Explore Enhanced Security with Conditional Access Filters & Templates – Enhance IAM Now!
Key insights
The recent advancements in Conditional Access Filters and Templates enhance security and management for organizations using Microsoft Entra ID by allowing granular control over user access to resources.
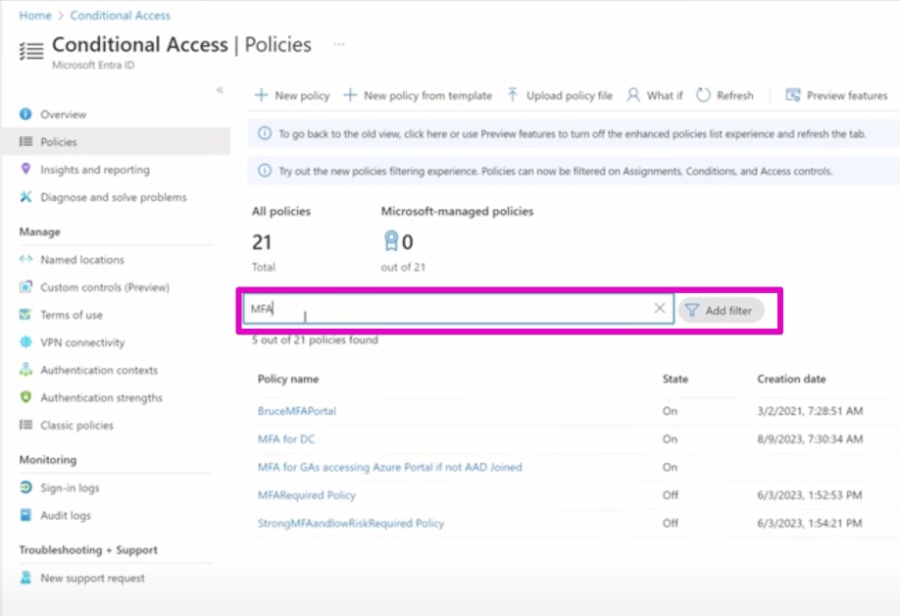
Conditional Access Filters enable the specification of criteria to include or exclude users, devices, and apps from policies, such as requiring multi-factor authentication for users on non-compliant devices or blocking access from certain regions.
- Enforce MFA from non-compliant devices.
- Limit application access to specific countries.
- Prevent application use from risky IP addresses.
Conditional Access Templates meanwhile offer preset policy configurations which adhere to common use-cases and best practices, streamlining the security implementation process.
- Mandate MFA for accessing cloud resources.
- Demand device compliance for corporate resource access.
- Facilitate hybrid work with MFA regardless of device or location.
The employment of these features leads to various organizational benefits, such as enhanced security through precise access controls, reduced administrative workloads thanks to simplified policy management, and improved regulatory compliance.
Conditional Access Filters and Templates are essential elements for bolstering the security and operational effectiveness of an organization's identity and access management strategies.
Conditional Access in Microsoft Entra ID
Conditional Access is a critical component of Microsoft Entra ID, providing organizations with the ability to enforce security policies based on specific conditions. It essentially serves as a gatekeeper, ensuring that only authorized users, under certain conditions, can access resources. Conditional Access brings a dynamic approach to security, going beyond traditional, static methods by adapting to the continually changing context of access requests.
By leveraging features like Conditional Access Filters and Templates, IT administrators can apply policies that are not only precise but also efficient and scalable, aligning seamlessly with the various demands of a modern, mobile workforce. Furthermore, these tools align with the goal of zero trust security models, wherein trust is never assumed and must be continually verified, thus significantly fortifying an organization's defense against potential breaches or misuse of sensitive data.
Enhancing Identity Management Practices
In the realm of digital security, enhancing identity management practices is crucial for safeguarding sensitive information and resources. The role of strategies like Microsoft Entra ID’s Conditional Access Filters and Templates cannot be overstated. They enable organizations to reinforce their defenses against unauthorized access, thus balancing security with flexibility. Utilizing these advanced capabilities, administrators can intricately craft policies relevant to their unique organizational demands. Ultimately, these features offer a more secure, streamlined, and compliant approach to identity and access management in the ever-evolving landscape of cybersecurity.

People also ask
What is the limitation of Conditional Access?
Conditional Access policies are powerful for securing resources in Azure, but they have limitations. Policies may not provide controls for some fine-grained scenarios, and there can be a maximum number of policies that an organization can enforce. Additionally, Conditional Access policies depend on the user's subscription level and might not be available in all licensing tiers.How do I exclude filtered devices from Conditional Access?
To exclude filtered devices from Conditional Access, administrators can set up exceptions in their policies. This is usually done by specifying conditions or filters based on user groups, device types, or other attributes to segregate the devices that should not be subjected to the Conditional Access policy.What are the different types of Conditional Access?
Conditional Access in Azure can take various forms, including user-based policies, device-based policies, app-based policies, location-based policies, and risk-based policies. These can be combined or used individually to enforce access controls determined by the organization's security needs.What is CA policy in Azure?
In Azure, a CA (Conditional Access) policy is a set of rules that determines the conditions under which users and devices can access cloud apps and services. It allows administrators to apply the right access controls when needed to keep their organization secure while providing a seamless sign-in experience for the end-users.
Keywords
Conditional Access Filters, Access Control Templates, Conditional Access Policies, Access Management Filters, Conditional Templates Security, Identity-Based Access Filters, Cloud App Security Conditions, Conditional Access Rules, Dynamic Access Templates, Conditional Access Configuration