- All of Microsoft
Optimize Security with Conditional Access & Auth Flows
Principal Cloud Solutions Architect
Boost security with Conditional Access & Authentication Flows guide by MVP John Savill. Stop phishing in its tracks!
Key insights
- Conditional Access (CA) and Authentication Flows offer enhanced security in digital environments, enabling IT admins to enforce granular access controls.
- Authentication flows define how users sign in, with methods ranging from traditional passwords to Multi-Factor Authentication (MFA) and FIDO2 security keys.
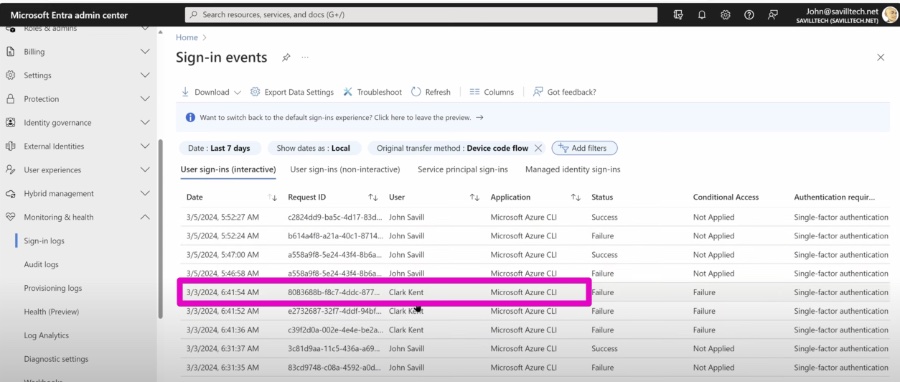
- CA policies can block or restrict risky authentication methods, like the device code flow, enhancing protection against abuse.
- Implementing CA with Authentication Flows allows for stronger authentication enforcement and the mitigation of phishing threats by blocking unexpected sign-in attempts.
- To set up, locate authentication flows in the Azure AD Portal, create a new policy with specified assignments, conditions, and access controls, then enable the policy for enforcement.
Understanding the Importance of Conditional Access and Authentication Flows
As cyber threats evolve, securing user identities and access points becomes a critical challenge for organizations. Conditional Access (CA) and Authentication Flows in Azure Active Directory (Azure AD) offer a sophisticated solution to this problem. By allowing IT administrators to set detailed access policies based on user, device, and location signals, organizations can significantly improve their security posture. Authentication Flows, including password-based authentication, Multi-Factor Authentication (MFA), and FIDO2 security keys, play a crucial role in defining secure sign-in procedures for applications. These methods, when integrated with CA policies, enable targeting and mitigating risks posed by certain authentication methods deemed vulnerable to attacks, such as the device code flow.
John Savill's [MVP] sheds light on strengthening IT security through Conditional Access (CA) and Authentication Flows in a recent video. Integrating CA with various authentication flows enhances security by allowing granular access control. This approach is crucial in a digital era where security threats are increasingly sophisticated.
Authentication flows define the process through which users access applications, varying from password-based methods to more secure options like Multi-Factor Authentication (MFA) and FIDO2 security keys. Each flow has its unique benefits and vulnerabilities, making it imperative to choose wisely to safeguard sensitive data.
Conditional Access policies analyze signals such as user identity, device, and location to decide on access permissions. By targeting risky authentication methods, enforcing stronger authentication, and mitigating phishing, CA policies significantly enhance security. For instance, device code flow, prone to abuse, can be selectively blocked or restricted to trusted environments.
To set up Conditional Access with Authentication Flows, administrators must first identify the authentication flows within the Azure AD Portal. Following this, a new CA policy can be created, specifying users, groups, apps, conditions, and access controls. It's recommended to start with "Report-only" mode to assess the policy's impact before full enforcement.
Example use cases include blocking the device code flow for most users while allowing exceptions for admins in trusted locations and mandating FIDO2 security keys for accessing high-security applications. Restricting legacy authentication through CA policies could also help in phasing out outdated protocols.
Prior to implementing these policies, understanding the organization's authentication patterns is crucial. Additionally, educating users on new authentication requirements and continuously monitoring CA logs for adjustments ensures both optimal security and usability.
In conclusion, leveraging Conditional Access alongside authentication flows allows IT administrators to safeguard access to company resources effectively. This proactive approach ensures that only authorized users can access sensitive data under stringent conditions, thereby enhancing the overall security posture against increasingly innovative attackers.
About Authentication Flows and Conditional Access
Exploring the Depths of Authentication Flows and Conditional Access
Conditional Access and Authentication Flows stand at the forefront of modern cybersecurity measures, offering robust protection against unauthorized access. These mechanisms work synergistically to create a secure IT environment, essential for safeguarding sensitive information in today's digital landscape. By implementing Conditional Access policies, organizations can dictate the terms of access based on specific conditions, ensuring that only verified users can navigate through critical infrastructure. Authentication Flows add another layer of security, determining the manner in which authentication occurs and offering varied methods to meet different security needs. From traditional passwords to advanced FIDO2 keys, these flows adapt to security requirements, ensuring flexibility without compromising on safety. As phishing and other cyber threats evolve, the ability to fine-tune access controls becomes indispensable for protecting assets. By thoughtfully integrating Conditional Access with Authentication Flows, companies can reinforce their defenses, ensuring that they stay ahead of potential threats while maintaining efficient access for legitimate users.

People also ask
Questions and Answers about Security & Identity/Microsoft Entra
"What is Conditional Access authentication?"
Conditional Access leverages various signals before making decisions on granting access. These signals encompass user or group membership, allowing policies to specifically target users and groups which provides administrators with precise control over who accesses what."What is the limitation of Conditional Access?"
There's a cap on Conditional Access policies, limited to 195 policies per tenant. This encompasses all Conditional Access policies irrespective of their status, be it report-only, active, or inactive. It’s advisable to categorize your applications by their resource needs and the user groups requiring access to manage this limit effectively."What is the best practice for Conditional Access policy for MFA?"
For bolstering security in your Microsoft 365 environment, it's recommended to implement 9 critical Conditional Access policies. These include restricting logins from specific countries, disallowing unused device operating systems, mandating device compliance, insisting on Hybrid Azure AD joined devices, enforcing application protection policies, blocking users or sign-ins with high risk, and the mandatory requirement of Multi-Factor Authentication (MFA)."How do I enable MFA through Conditional Access?"
To enforce MFA through Conditional Access, go to Access controls > Grant, select Grant access and Require multifactor authentication, then hit Select. Confirm your configurations and adjust Enable policy to Report-only before selecting Create to activate your policy.
Keywords
Conditional Access, Authentication Flows, Multi-Factor Authentication, Azure AD, Security Policies, Access Management, Secure Login, Cloud Security